Working with QPC Security
Frequently Asked Questions
What makes QPC Security different?
First, and foremost, our experience and our team. We are different because we think different. Not only do we have 25+ years of experience, but our team is also comprised of engineers, architects, information security officers, compliance experts, and people who care a great deal about the operational maturity and information security of your organization.
We are not general business entrepreneurs who decided to get into the technology game because it is a hot market; we have the technical know-how and experience to solve your real-world technology and security problems. We don’t have sales and account managers that get paid based upon closing deals and upselling clients. We rely on our expertise and reputation to communicate our value to prospective clients. In fact, our President and CEO Felicia King is considered to be one of the top network layer and cybersecurity strategists in the country.
The QPC Security team is dedicated to continuing our education and staying abreast of all the changes in the IT information security sector. We have the certifications and training to prove our knowledge and experience. A word of caution here – many MSP/MSSP/vCISO say they have certifications and training, but they do not have the documentation to support those claims or the peer recommendations QPC Security enjoys.
Do I receive a quote for services after a phone call/initial meeting with QPC Security?
No. Solving complex technology and network security is a nuanced process. It involves collaboration with your organization to understand your business, followed by an assessment to gauge the risks your organization needs to address. After the assessment, a strategic plan and high‑level engineering plan will help drive the solution and result in a budget. Until we understand your existing environment, and the risks you need to mitigate, we cannot provide a plan to move forward. Your solution must be engineered to deliver desired outcomes in alignment with a mutually agreed strategic plan.
As an analogy, consider you purchase a piece of undeveloped land in a rural part of your state. You plan to build your ‘dream home’ on this parcel. You have an introductory call with a custom home builder and share your vision of having a 6 bedroom, 5 bath home with a three-car garage and finished basement. Would it be realistic for you to expect a quote from that builder after that phone call? Of course not. Until soil tests are conducted, local building codes addressed, utility availability assessed, materials selected, etc., a builder will be unable to provide a realistic, legitimate quote on how much your dream home will cost.
Finally, we encourage any organization considering a partnership for MSP/MSSP/vCISO services to be wary of a company that provides a quote after one discussion. Unless they already know your environment in-depth, their quote may likely be based on making assumptions and applying a cookie‑cutter fix to your problems.
Our insurance carrier needs us to complete a cyber security assessment. Can QPC Security help us with that?
Before we answer the question about insurance providers’ cyber risk assessment questionnaires, let’s think about why your insurance carrier wants the assessment.
Cybersecurity risk insurance is fairly new, compared to other provisions of insurance. Over the past 30 years, as more and more large, medium, and small businesses have suffered cyber and fraud attacks, there appear to be two options: 1) ensure that your organization is so secure and fail-proof that the risk of an attack is almost not a concern; 2) obtain an insurance policy that will offset or cover the costs of an attack, because it is so difficult to ensure 100% security.
As cybersecurity risk insurance policies were sold and businesses were attacked, these insurance policies began to be tested within the US court system. While judgments have fallen on both sides of the parties involved, insurance providers quickly saw a need to gain attestation from their customers that, indeed, the businesses had certain basic cybersecurity hygiene and best practices in place. If the business does implement sound security practices, they may be insured with a higher liability limit; to put it another way, the business is more insurable.
If the business does not have sound cybersecurity best practices, then they are a higher risk; in fact, an organization without basic cybersecurity hygiene may be found to be uninsurable. In a worst-case scenario, where your organization is attacked and the insurance provider denies the claim, your attestation of cybersecurity best practices within your organization may come under scrutiny in a court of law.
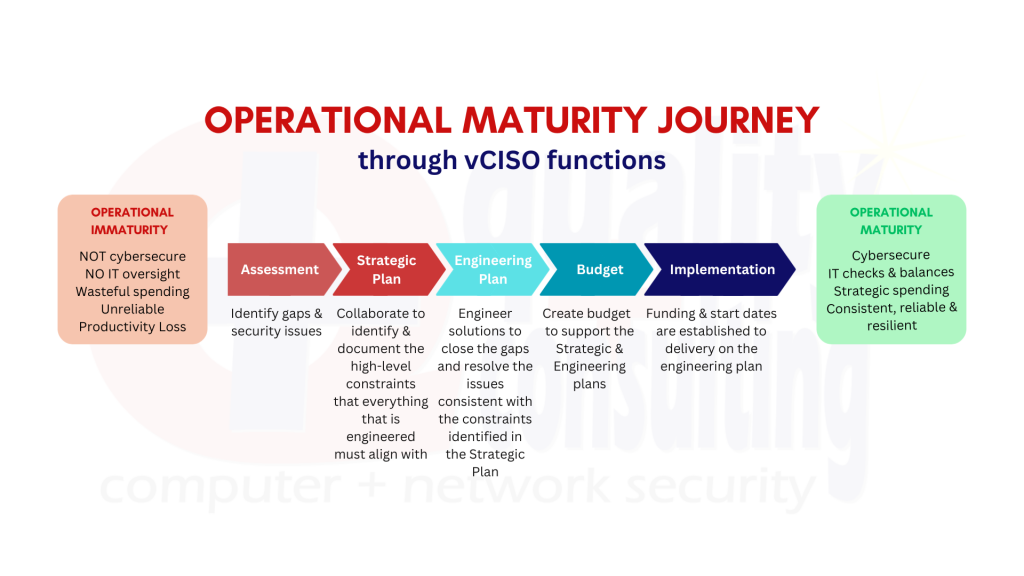
So, to answer the question, yes and no. We can conduct an assessment, create a strategic plan, formalize an engineering plan, and help you put the pieces required for basic cybersecurity hygiene together to best protect your customers and your organization and to confirm your insurability. By correcting security gaps, an organizations’ risk is not only reduced, but compliance with requirements from insurance carriers, banks, vendors, customers, and state law are accomplished. For additional clarity, refer to the diagram that describes the Operational Maturity Journey. Details of that journey are also described later.
Alternatively, if your organization is looking for someone to review the questionnaire and answer the questions in a manner that will suffice for your insurance renewal, we are not the security consultant for you. First, to simply answer the questions without having a valid idea of cybersecurity within your organization is a legal liability for QPC Security. Second, it is a disservice to your organization as doing so would result in a fraudulent response. One of the biggest mistakes we see organizations make within the current cyber insurance and cyber-risk space is waiting until the last minute to review and complete the questionnaire and then risk loss of coverage. For more information on this topic, listen to our Breakfast Bytes podcast segment "Avoid Cybersecurity Insurance Fraud".
What is the vCISO Journey to operational maturity?
A vCISO is a virtual information security officer. A vCISO offers their experience and expertise to small and medium-sized organizations to create, maintain, assess, and revise the organization’s Information Security program and posture according to the risks and needs of the organization. Primarily, a vCISO assists SMBs with progressing from operational immaturity to operational maturity, as shown in the graphic below and described in the paragraphs that follow.
During an assessment, we locate where all sensitive information about your customers and your company resides and how it is used. We look at the security controls already in place, including backups, passwords used by staff, and the overall security posture, and assess the ability for the controls and how they are currently being used to protect the information. From these two pieces of data, we are able to identify gaps between existing controls and maximum reduction of risk, and provide recommendations to close the gaps. We also assess the organization’s overall security posture.
The assessment and recommendations provide the outline for the information technology (IT) strategic plan. An IT strategic plan, according to Wikipedia, is “a specific type of strategy plan that lets an organization know where they are now and where they want to be some time in the future with regard to the technology and infrastructure in their organization.” Your IT strategic plan is a collaborative effort between your organization and QPC Security, and will include priorities for security and privacy best practices, provisioning of hardware and software for the lowest total cost of ownership over time, and allows for honest responses to cyber security insurance questionnaires over the next few years. The IT strategic plan is both an immediate plan for getting to a cybersecurity baseline and a future mapping to maintain and go beyond basic compliance.
From the strategic plan, an engineering plan and a realistic budget are formed. The engineering plan describes the nuts and bolts of bringing the strategic plan to life within the organization and requires a specific solution unique to your business and its needs. While the engineering plan will have some specific details regarding implementation, it is just as much a forward-thinking document relating how to maintain the cybersecurity posture over the years to come.
The budget outlines the resources required to accomplish these efforts. Here, resources are not only the dollars and cents, but also includes time and people. It is almost impossible to set a realistic budget to remediate the gaps in the current environment and to accomplish cybersecurity best practices and operational maturity without an engineering plan. It is worthwhile to keep in mind that the engineering and budget planning processes take weeks, and sometimes months, of time to scope and develop. However, these two elements bridge the gap between the strategic plan and the implementation phase.
Finally, the implementation of the strategic and engineering plans begins. This is the project and process phase of the engagement, where the assessment, plans, and budget result in hands-on products and services for your organization. Implementation is both static and dynamic; it is a one-time occurrence that solves an immediate issue or problem and it is a long-term commitment with a provider that allows you to relax and trust that your organization is protected and insurable.
Learn more about our vCISO services.
How much does it cost to conduct a thorough cyber security assessment and get us to a cybersecurity baseline?
Until we have a chance to assess your specific environment and discuss your short-term and long-term needs, it is impossible to provide a quote. QPC Security cannot and will not provide ‘over the phone’ types of estimates, as the quote is likely to be unreasonable and insufficient to both parties. That said, there are some typical averages for the components of the cybersecurity assessment process.
We recently conducted an initial assessment in under three hours. Due to our 25+ years of experience in conducting assessments, we were able to determine the current security posture and identify the controls needed to mitigate the organization’s risks without installing additional software. We produced a findings document, then reviewed this information with the C-level and IT manager for the organization. At this point, we had invested 20 hours into the effort.
The next step was the creation of the engineering plan with budgetary figures; this was expected to take 25 hours, bringing the total hours involved to 45 hours to conduct the assessment, document the gaps, create a plan to close the gaps, and agree upon the necessary budget. It is important to note that two other ITSPs recommended and quoted unnecessary server technology and failed to identify major security gaps in the environment. Fortunately, two of the organization’s board members are IT savvy; when they reviewed QPC Security’s security findings and issues document, they understood the severity of the identified issues.
As an aside, please beware of any IT services provider that quotes a monthly managed services fee of $2,000/month, with a one-time onboarding fee of $2,000, without conducting an assessment, developing a plan, and creating a budget to support the plan. From hearing the stories of other organizations making this mistake, the longer-term costs were exorbitant. The monthly rate of $2000/month was not enough to cover the additional projects that were uncovered or discovered after signing and being locked into a contract for insufficiently quoted managed IT services. For this reason, it is crucial that you are not misled by what appears to be inexpensive or affordable IT services and need to be sure that the assessment is done by an IT and security professional with the direct engineering experience and expertise to address all the IT and security problems you may have. Typically, sales engineers or account managers, are not prepared to provide an accurate assessment of your current environment.
In the example we started with, we have invested over 45 hours thus far. From one business to another, you likely understand that QPC Security cannot do this work pro bono, any more than your business could provide 45 hours of work for free. Our experience and knowledge in making reasonable assessment of your current environment and helping you achieve cybersecurity compliance need to be viewed as an investment that will help you make an informed decision and, ultimately, protect your organization and your customers.
As the business owner, do I have to be involved with technology-related planning?
Ideally, yes.
The primary reason you need to be involved with technology- and security-related planning is that when a cyberattack or other security incident occurs, as the business owner you will be held responsible for the overall security posture of the organization. Any compliance fees or costs to defend against or recover from an attack will also be your ultimate responsibility. Finally, your cyber risk insurance provider maintains any and all attestations to the security of your business as your statement, even if we assist in completing their annual questionnaires. The signature on the insurance application is yours.
As a business owner, you have a level of confidence when dealing with your organization’s financials, human resources, general business practices, sales, and maybe even legal requirements. As the final decision maker for your business, you regularly meet with your CPA, corporate attorney, and insurance company throughout the annual year.
Likewise, IT services, security, and planning require the same attention for you to make an informed decision and be part of the solution. We understand many aspects of technology seem daunting and confusing. Typically, the language and functions surrounding IT do not make sense or resonate with business owners without a minimal investment of time. We also know that technology in general brings about fear, uncertainty, and doubt (FUD). Knowing this, we make it a priority to discuss IT-related issues in a way that everyone can understand and be involved in the process and we work with you to minimize the FUD and assist in making the best strategic decisions for your organization. In fact, we insist on it.
We have a long track record of successfully educating our clients. Typically, when a relationship starts, we seek to have regularly scheduled meetings with clients and use every interaction to improve our clients’ understanding of IT issues while we learn more about their business. If you do not make time for IT meetings, it is impossible to be an informed decision maker.
As well, without regular meetings and taking the time to learn a little about what you need, your IT budget process will be frustrating and perceived as a simple cost center without our collaborative interactions. Only through discussion are we able to become aware of the challenges your organization faces and provide reasonable and effective solutions. We will likely be able to offer suggestions on leveraging what you already have or guide you to use an already vetted solution to solve a problem.
Can I just have my IT person/team communicate with you and relay the information to me?
While this seems like this would be the easiest path for you, when it comes to the cyber assessment, strategic planning, and engineering plan review, the answer is no. Every stakeholder that is going to play a role in the decision-making process, from understanding the direction of the business, to signing contracts, to purchasing decisions, needs to be involved every step of the way. Of course, C-level staff and other non-IT-related staff won’t need to do any actual IT or security work; however, everyone involved, even in a minor way, needs to be aware of what is happening and what is planned.
This requirement works both ways, too: From experience, we have learned that it is unproductive and impossible to realize true results when we have conversations with C-level staff and other key stakeholders, and then they delegate communications to their IT team who, in effect, become the ‘middlemen’. If questions arise related to the assessment process, strategic plan, or engineering plan, we must have open lines of communication directly with you and the stakeholders. Passing questions and responses through a chain of people instead of covering the questions and discussing the long-term needs with all parties involved at once is inefficient, causes frustration, and prevents sound decision-making.
Do you replace our current in-house IT?
Hopefully not. Our goal is not to replace your in-house IT unless that is your need. The optimal arrangement is for QPC Security to work with you, the business owner, and your internal IT team to ensure you achieve operational maturity as it relates to your internal IT and a sound cybersecurity posture.
It is unrealistic to expect internal IT staff to know and do everything. Your organization may have an excellent IT manager who is able to handle day-to-day support and maintenance. They may have been with your organization for over a decade and be very loyal and dedicated to the business. They likely hold vast long-term institutional knowledge. They may do a lot of minor IT projects for the organization. They are, indeed, a valuable part of your team.
That being said, they may not have the skillset and experience in order to conduct an accurate, detailed assessment, strategic plan, engineering plan, and know how to research solutions for a fully vetted implementation plan. Internal IT also lack test labs where they can fully vet configurations. When QPC recommends solutions to clients, they are solutions that QPC uses themselves, that have been vetted and implemented. QPC develops and refines standards and implementation guides for all systems they support. If you expect internal IT to implement or recommend solutions, they do not have the resources that QPC does in order to validate that a strategy or solution is able to deliver an outcome. The ramifications of this can be hundreds of thousands of dollars wasted on an implementation that should not have happened.
Too often, organizational leadership consider they can abdicate authority for the responsibility of IT decision-making by delegating authority for all IT decisions to the internal IT team. Problems occur when an organization’s leadership has a misperception about the magnitude of what in-house IT can or should be doing. The results are bad decisions that cost many organizations time, money, and productivity.
The best solutions are developed collaboratively and benefit from the institutional knowledge of in-house IT staff, organizational leadership, and a highly experienced ITSP business partner. Many organizations function best with someone physically present at the main office who can immediately respond to end user support requests. As well, in-house IT benefit when they can coordinate with the managed services business partner to determine the best solutions for the organization overall and to allow the most efficient use of their time.
Take, for example, the system backups of your critical customer and organization data. In the event of a natural disaster, a ransomware cyber-attack, or some other unforeseen event, the only ‘insurance’ you have which guarantees that you are able to continue operations is a solid backup of your data and applications coupled with excellent pre-planning and proper resiliency. In this context, backups of your critical internal systems are crucial and the backup process, as well as the ability to restore from the backups, needs to be reviewed and validated by both internal and external IT personnel. Gaps in this process, and that threaten your return to business-as-usual after an event, should be addressed by you, your internal IT team, and a qualified external IT provider. It is only by bringing all parties to the proverbial table that your organization can truly be strategic about your technology systems and security posture.
Consistency, reliability and resilience occur within an operationally mature organization. Without operational maturity, there are chaotic decisions, performance gaps, inefficiencies, and security gaps that open your organization to cyberattacks.
Do you help us make purchasing decisions?
Yes, we can and we will! One of the key deliverables coming from the strategic and engineering plan development is a procurement policy. A procurement policy eliminates abstract and loose decision-making when it comes to technology purchases and ensures your organization only invests in products and services that align with the strategic and engineering plans.
It is very common for an organization to make poor decisions related to technology purchases because they had no procurement policy and made a purchase based on price or a feature. Purchasing technology and network equipment in this way, without knowing whether or how the new asset will fit into the existing network or produce the desired results, is a waste of money. Many times, it creates a new security risk where one did not previously exist.
We have clients who will say, after purchasing an expensive piece of equipment or software, “We didn’t think we needed to consult with you about the purchase.” This is usually after they made an inadequate, but hefty purchase and then ask us to help them fix it. Of course, the new accounting software program may have cost $30,000 less than another program on the market; to make it operable, though, can result in the final price tag being six figures.
A procurement policy will verify purchases are made using sound methodology and prevent expensive and sizeable mistakes that result from unfortunate decisions.